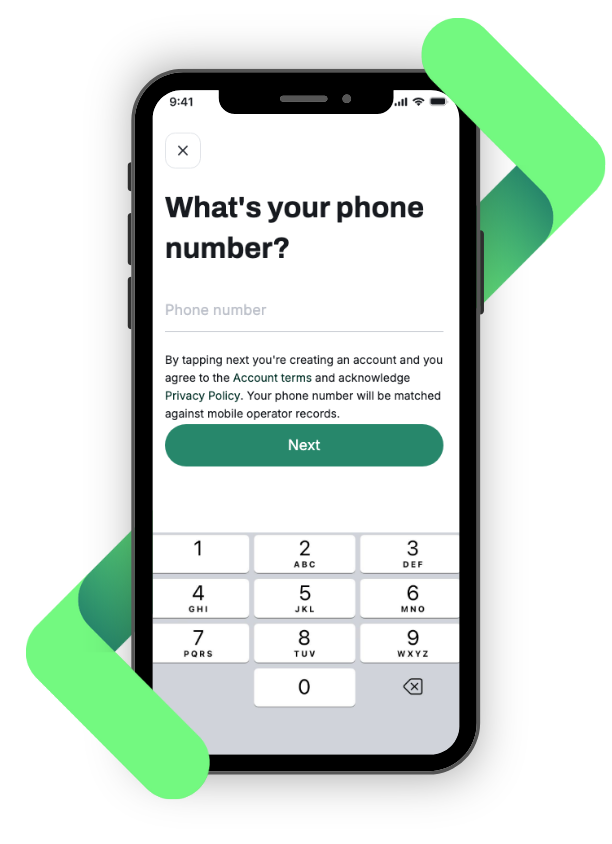
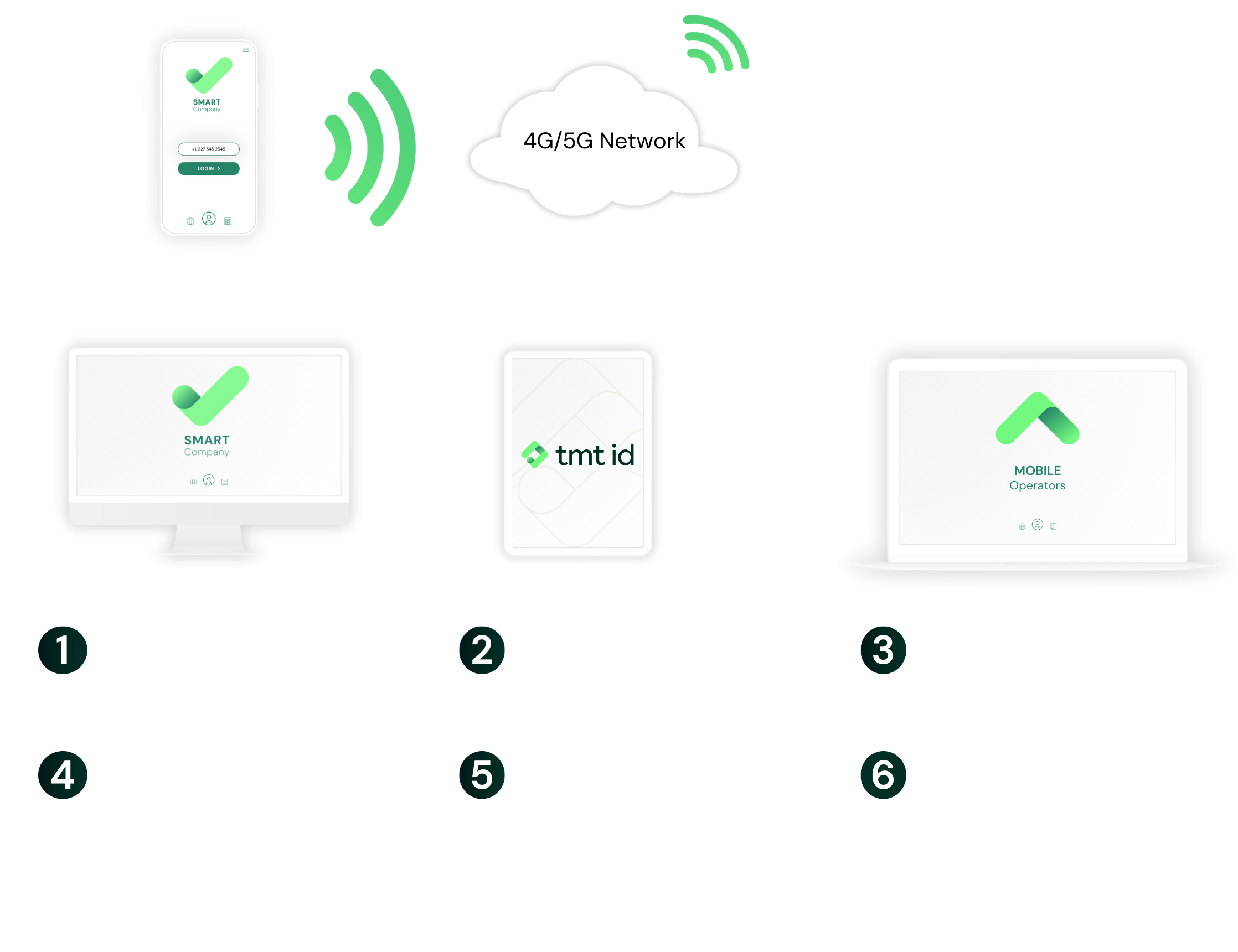
First, we identify the current mobile operator of the phone number. Then, working in real time, we connect to the mobile operator to confirm that the phone number matches the one registered on the user account. Optional SIM-Swap checks can then flag whether the phone number has had a recent SIM change. Everything happens in seconds, so your app flow remains smooth